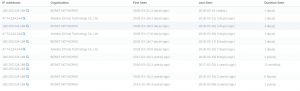
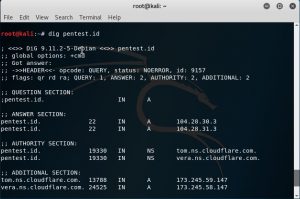
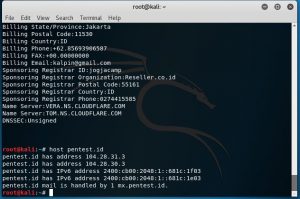
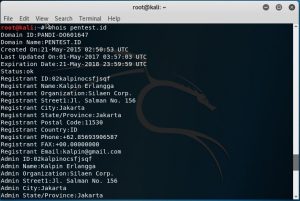
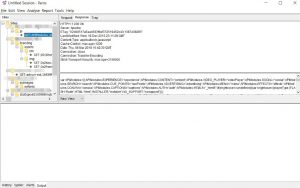
Last week, I learned to use online tools to discover old DNS and the real IP address behind the firewall. One of the online tools that I tried was dnstrails.com. In dnstrails.com, I could get so many information for a specific website such as the registrant, the registrar, the admin contact, the real IP, the other hosts that in the same server, the subdomains and many else. Moreover, I could also determine whether the emails that they sent in spf are as spam or not, it will be spam if the IP they’re using is different.
The records:
We could get address mapping record, IPv6 address records, mail exchanger records, name server records, start of authority records and text records.

History data:
We could get the old script, which may contain vulnerable code and the old admin page, which we could brute force it and other sensitive informations